Exercise 3.4: Troubleshooting¶
Objective¶
In this exercise we will examine the response pages, event logs and briefly look at utilizing HTTP capture tools
Task 1 - Response Pages¶
- Go to Security > Application Security > Policy > Response pages
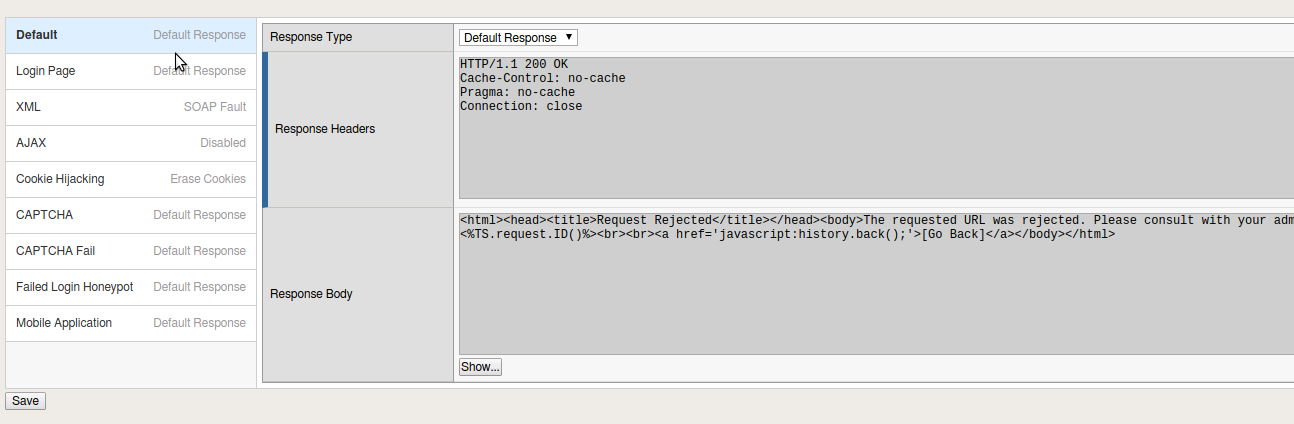
- Within this area you can add various response pages for different request. These pages can be modified by editing the response body. On the Default change the Response Type to “Custome Response”. This will open up the Response Body to editing.
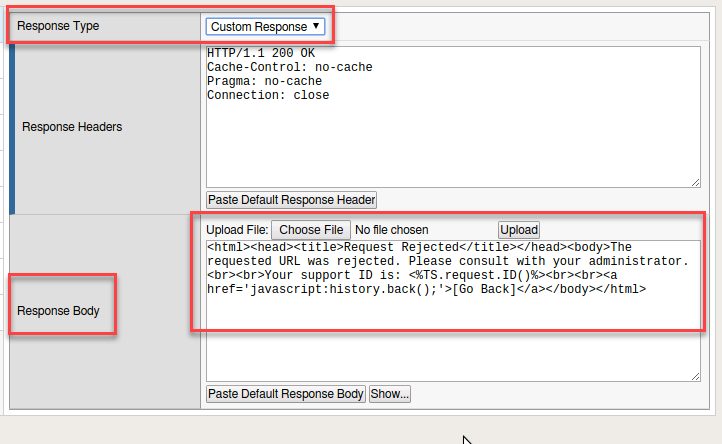
- Edit the Response as follows:
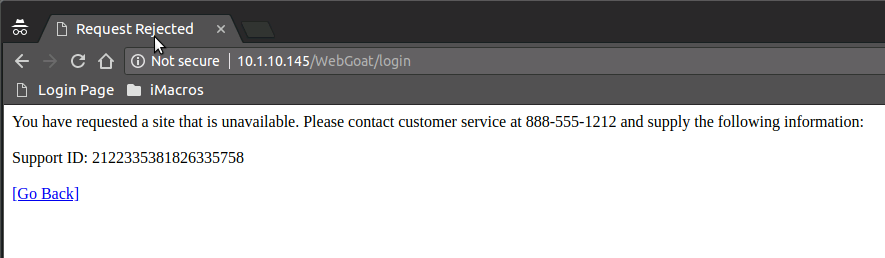
<html><head><title>Request Rejected</title></head><body>You have requested a site that is unavailable. Please contact customer service at 888-555-1212 and supply the following information:<br><br>Support ID: <%TS.request.ID()%><br><br><a href='javascript:history.back();'>[Go Back]</a></body></html>
- Click on the Show button
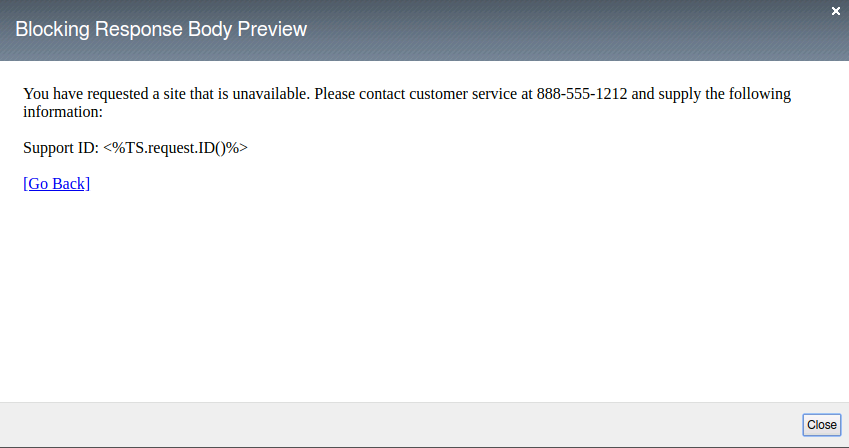
- Click Save and Apply Policy. And click OK.
Note
Explore the other response pages. Observe that AJAX reponse pages are disabled by default.
- Open a New Incognito Window in Chrome and navigate to the Webgoat login page
- Try entering a sql injection.
or 1='1
You should have received a reponse page that you customized. Make note of the Support ID before moving on to the next task.
Note
If you were to login to the web application again and try the SQL Injection do you think you will see a response page? What can you do to show a response?
Hint
Try enabling the AJAX reponse pages.
Task 2 - Event logs¶
- On the BIG-IP return to the Security > Event Log > Application > Requests
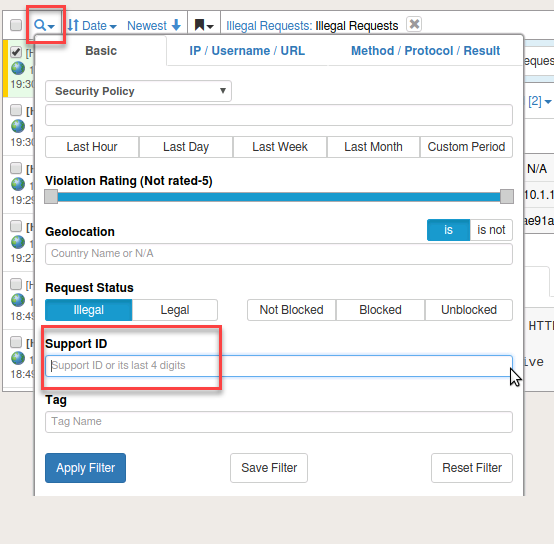
- Click on the magnifying glass and that will open the log filter. From here you can enter the Support ID you received from the preceeding task and select Apply Filter.
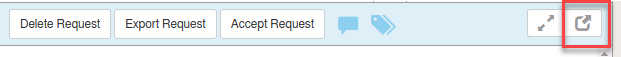
- Select the alert and at the top box you will find a button to open the request in a separate tab
- Click on Attack signature detected
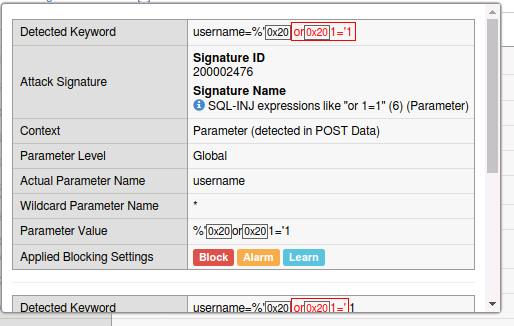
Observe the detected attack, the expected parameter, and what the applied blocking settings were. Also note that the signature used to block this attack has been identified. By clicking on the “i” next to the name you can get further information on the signature as well as a link to other documentation.
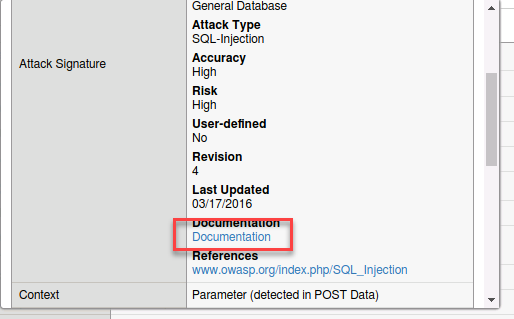
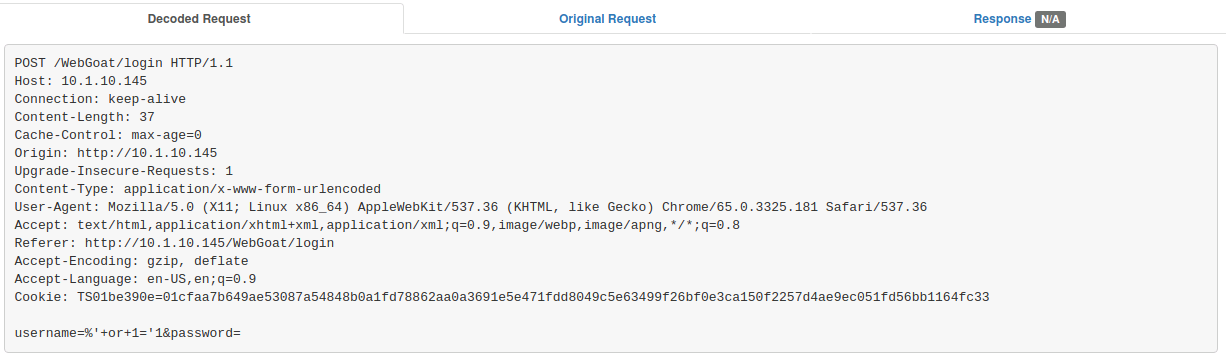
- Examine the http body information. Do you see your attack?
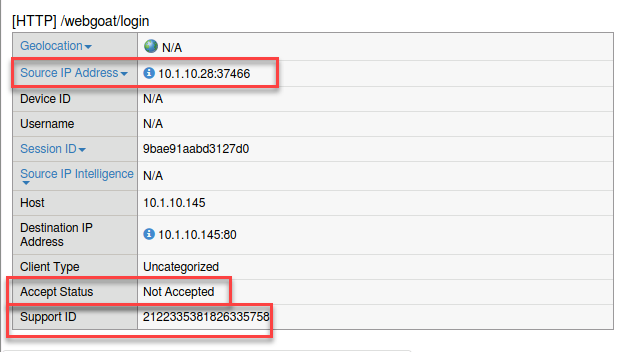
- Observe the Source IP, Accept Status and Support ID.
- Close this tab and return to the BIG-IP Event Logs. Open the filter again, remove the support ID, and click on Illegal and Not Blocked. Apply Filter
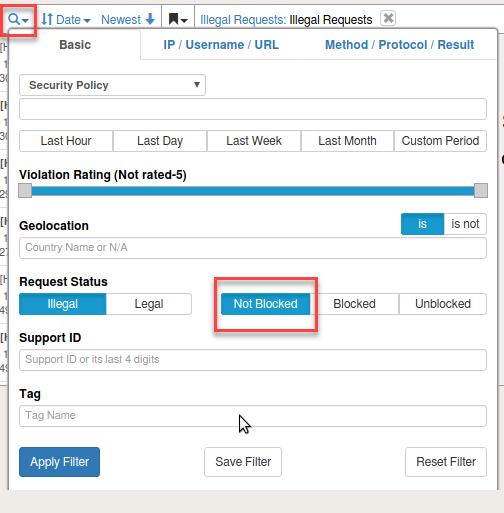
- Locate an entry and observe the Attack Type and Violation Rating
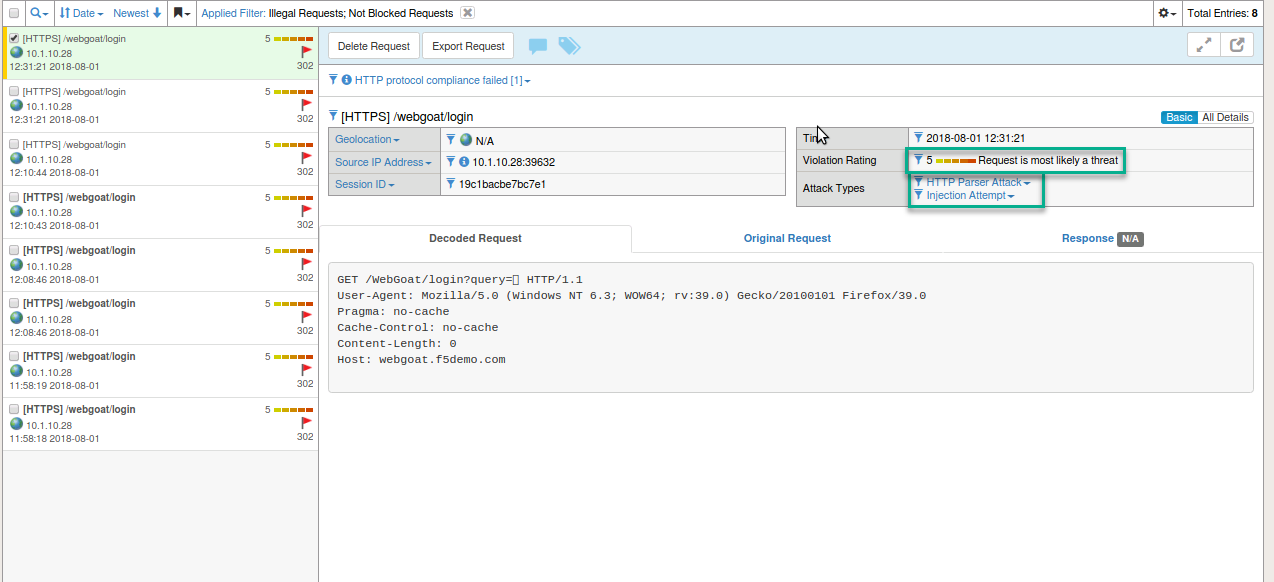
- Observe in the top left of the log you will find the Blocking Setting that could be enabled to block this request.
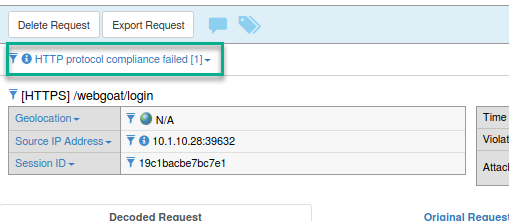
- Where would you find this setting to enable? What happens when you click on the link?
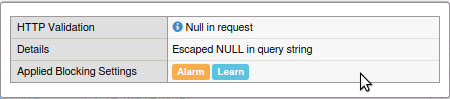
- Observe that the link will give you more information on which piece of HTTP Protocol Compliance will prevent this attack.
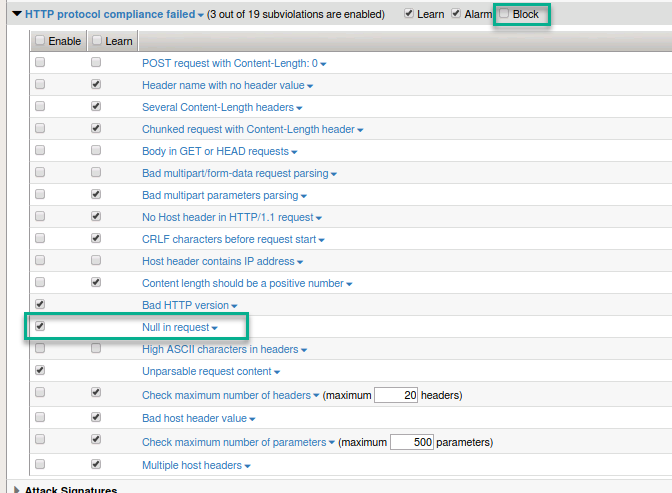
- Navigate to Security > Application Security > Policy Building > Learning and Blocking Settings and expand HTTP Protocol Compliance failed
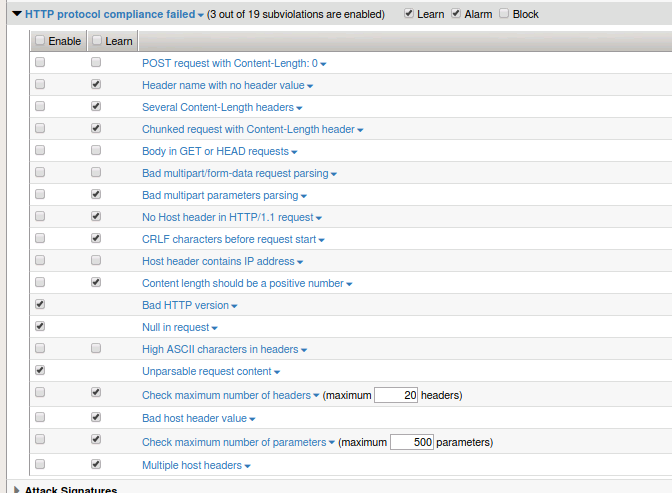
- Do you see the setting that would prevent this attack? How would you enable blocking for HTTP protocol compliance?