API L7 DoS attacks and TPS based protection¶
In this module you will examine L7 DoS attacks against API, detection and mitigation based on the transaction rate per second per individual source.
DoS profile configuration¶
- In the BIG-IP GUI navigate to Security -> DoS Protection -> DoS Profile and click Create; Define the name API_DoS and click Finished
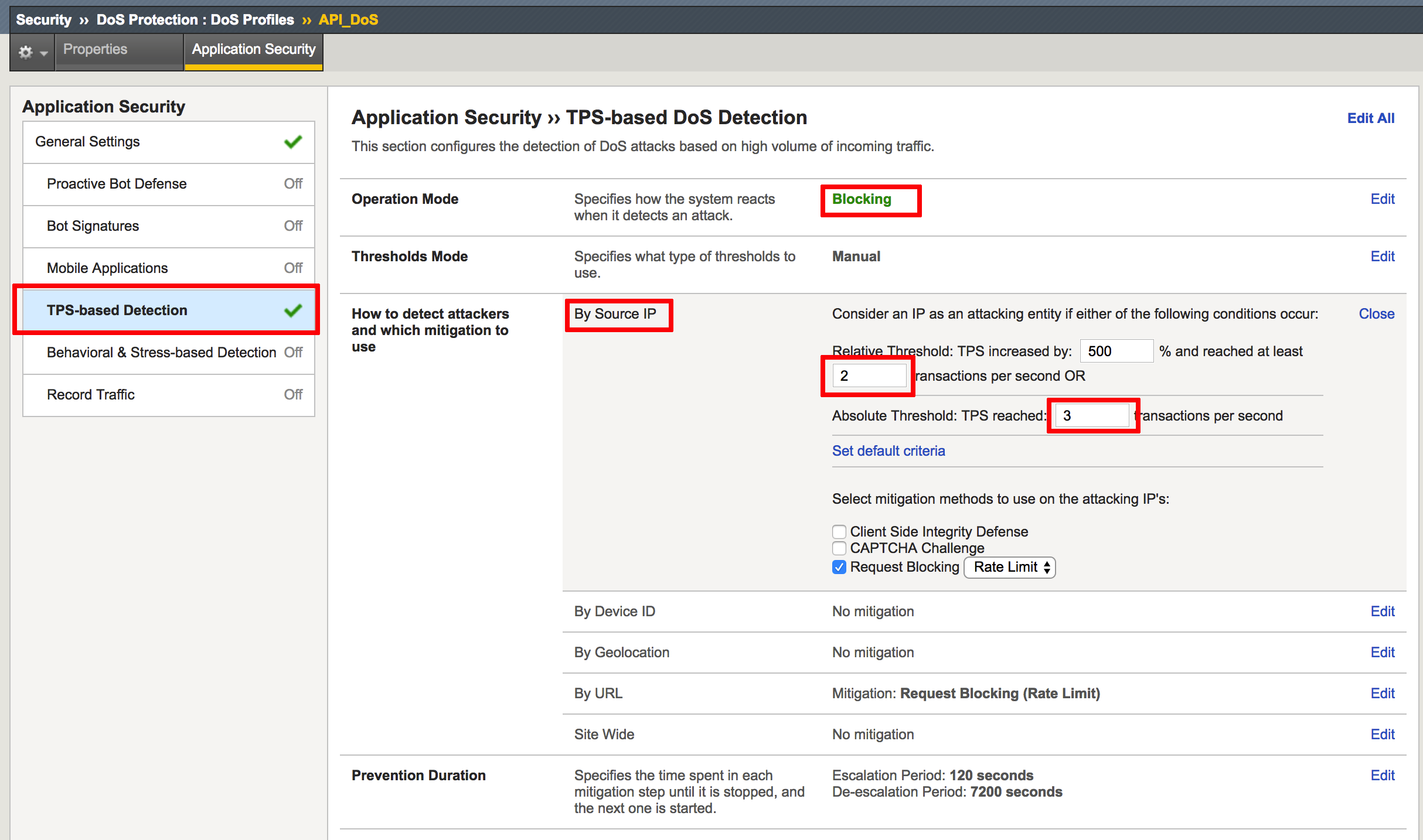
- Click on just created DoS profile and go to Application Security tab; click Edit, set the checkbox for enabled on Application Security and examine configuration options
- Proceed to TPS-Based Detection, make sure it is enabled and set mitigation criteria By Source IP: reached at least value to 2 and absolute threshold TPS reached to 3 tps, then click Update
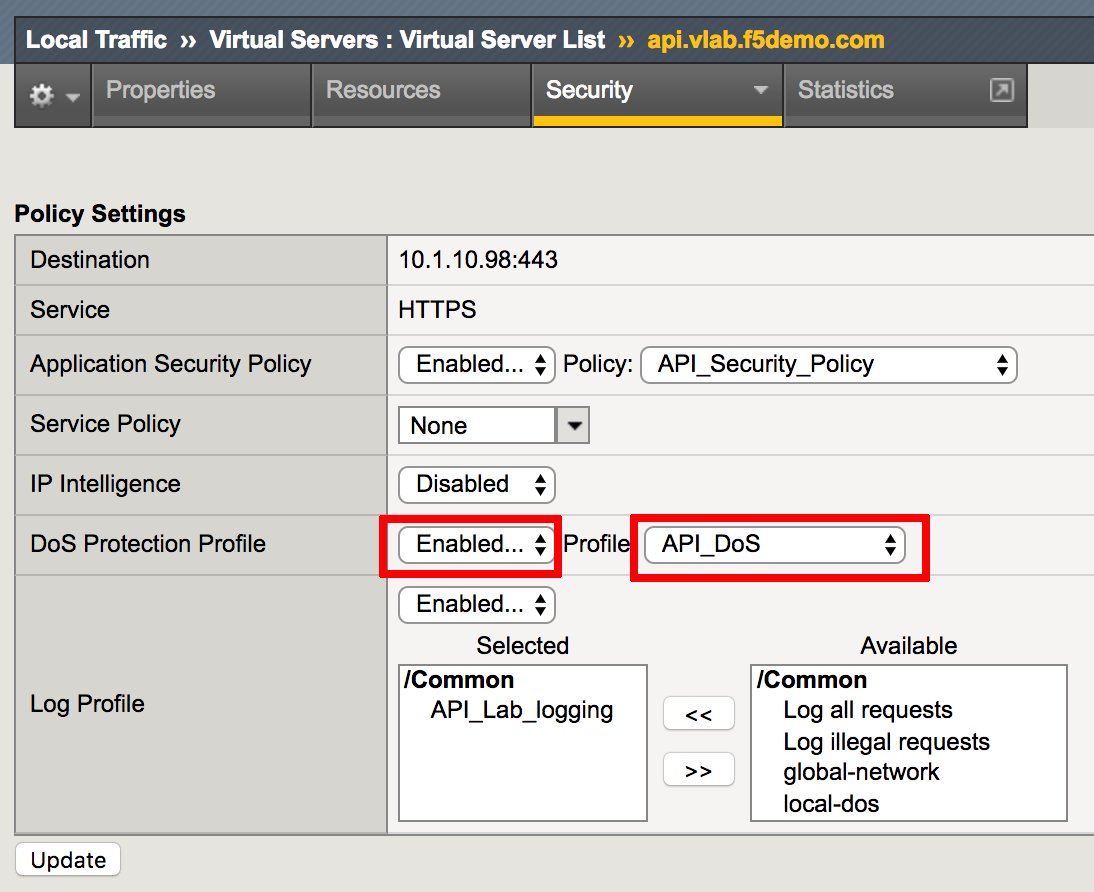
- Navigate to Local Traffic -> Virtual Servers -> api.vlab.f5demo.com -> Security -> Policies and enable DoS Protection Profile; choose just configured API_DOS profile from the dropdown menu
Examine protected API environment¶
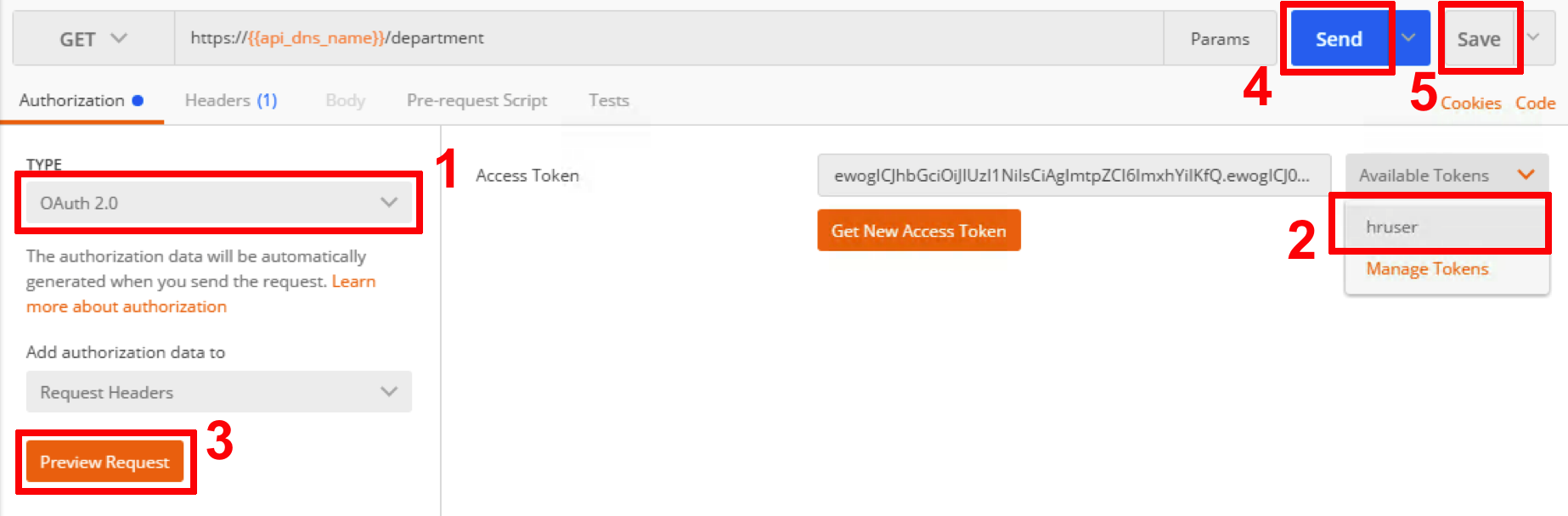
- Go to Postman, expand HR_API_DoS collection and click on DoS API call
- Make sure authorization type is set to OAuth 2.0. From the list of available tokens select hruser and click Preview Request. Then click Send. Make sure you are getting expected response and click Save
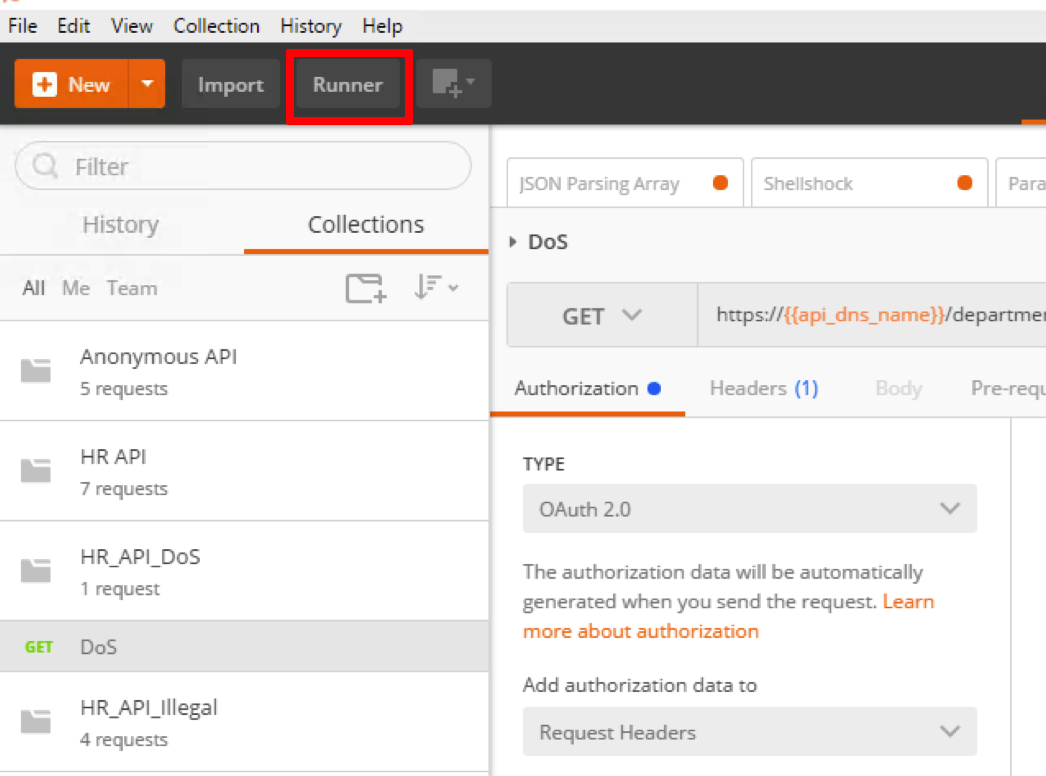
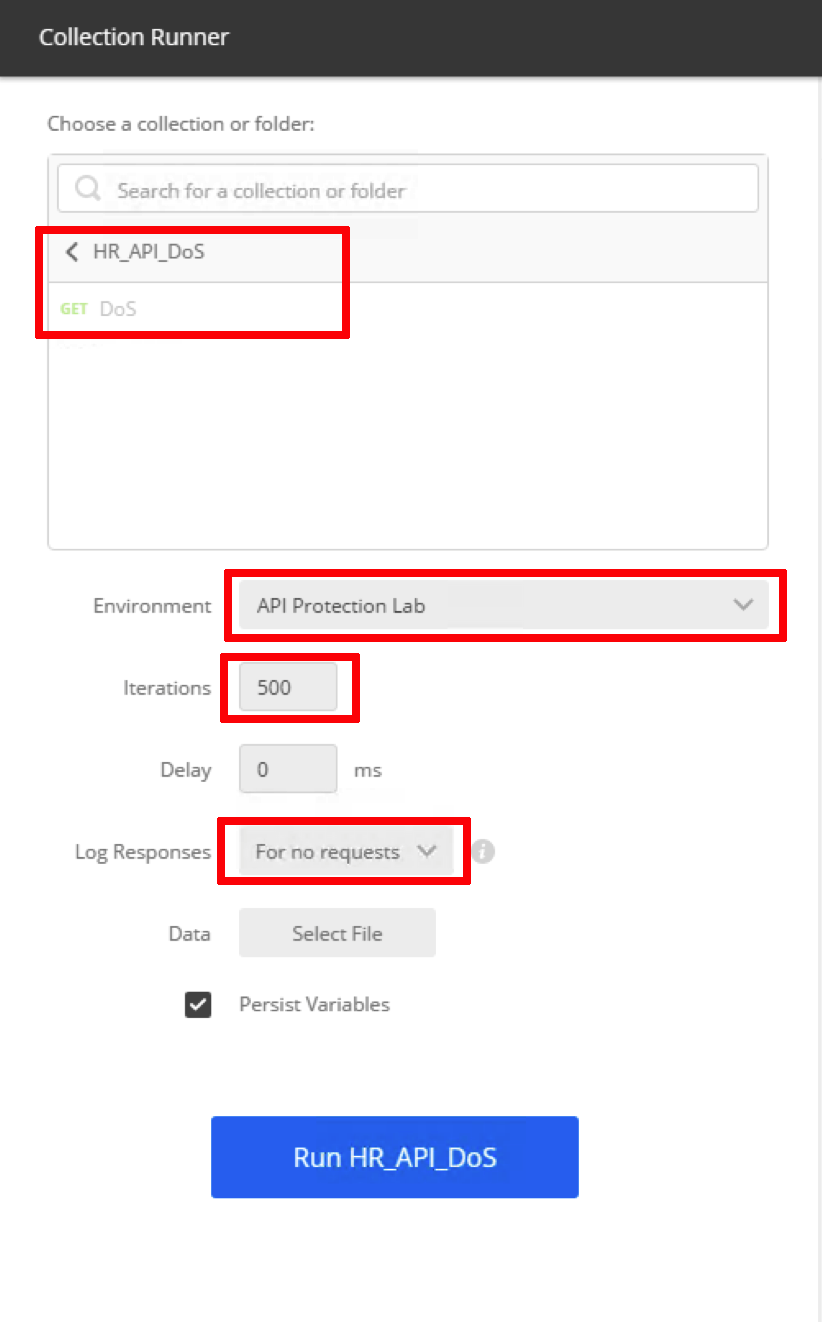
- Click Runner in the Postman
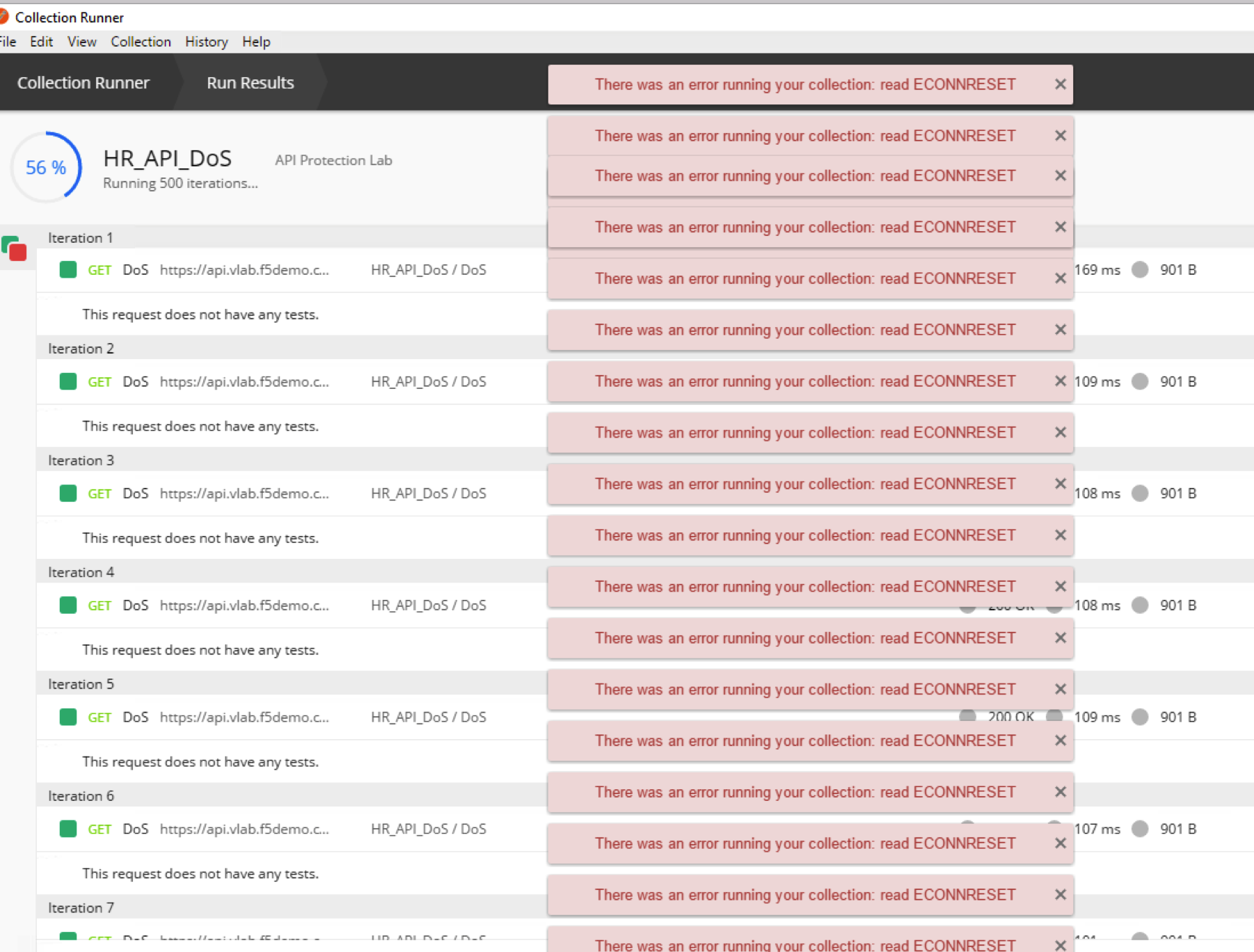
- Click on HR_API_DoS collection, select the Environment - API Protection Lab, set Iterations to 500, Log Responses set to For no requests and click Run
- After short period of time Postman Runner should report failing transactions (it may not and gracefully handle the rate limiting, proceed to check logs in next steps anyway)
- In the BIG-IP GUI navigate to Security -> Event Logs -> DoS -> Application Events and examine messages in the logs