Lab 8: XXE Protection¶
In this lab you will learn how to utilize ASM to mitigate the use of malicious XML External Entities
Connect to the lab environment¶
- From the jumphost, launch Chrome, click the BIG-IP bookmark and login to TMUI. admin/password
Note
While you can use firefox for connecting to the BIG-IP in this lab, you will be intercepting firefox traffic. It may be easier to use two browsers instead of two tabs.
- From the jumphost, launch firefox, which we will use to access WebGoat.
- In firefox go to the right-hand side icon and select “Preferences”.
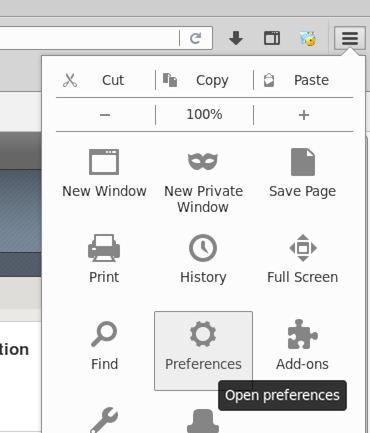
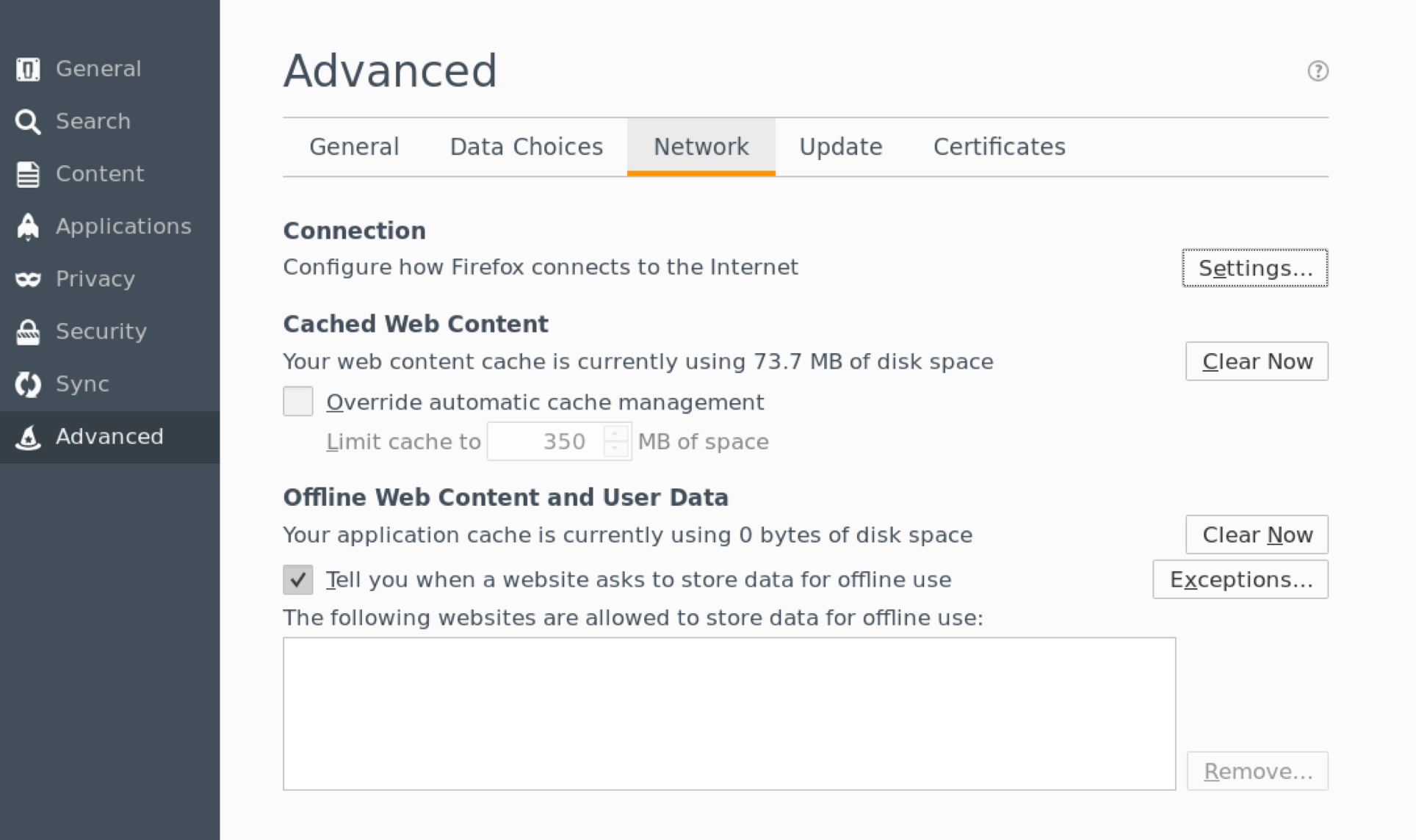
- Then select Advanced > Network, under “Connection” click “Settings”.
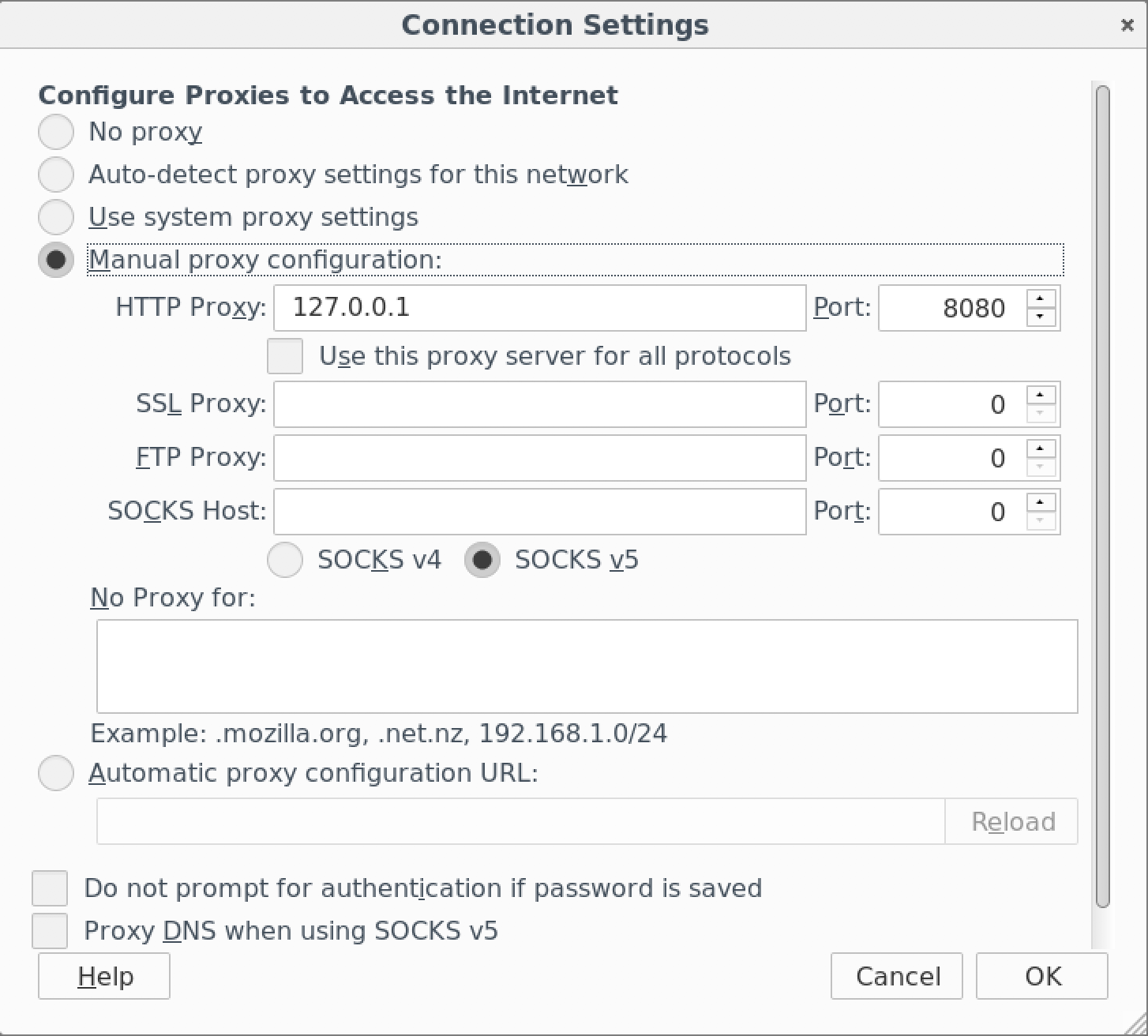
- Set your proxy settings to manual as shown in the screenshot below, click “Ok”.
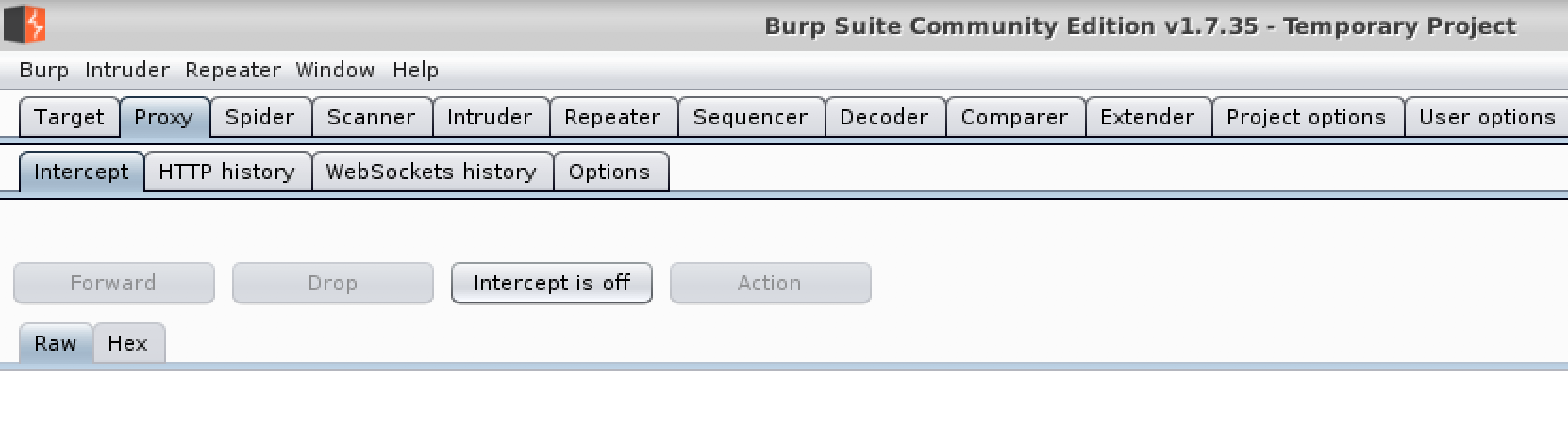
- From the jumphost desktop, launch Burp Suite using the icon on the desktop. If you are prompted to update Burp, ignore this pop-up by clicking “Close”.
- Select Temporary Projects and click Next.
- Leave Defaults checked and click “Start Burp”
- Select the “Proxy” tab and then turn intercept off.
An XXE Vulnerability¶
- Login to WebGoat using firefox f5student/password.
- Select “Injection Flaws” and then select “XXE”.
- If XML or XML External Entities are new to you, then please start from the begging and read through parts 1 and 2 in the WebGoat Lesson.
4. Under part 3, enter a comment to familiarize yourself with the application. To complete the lesson, you will need to figure out how to list the contents of the root directory utilizing this submission form.
- Enter the following statment in the field and click submit. What does this tell us?
:: &xxe;
- So we know that an XML External Entity can be utilized with this form, but we will need to manipulate a request.
Manipulating the Request¶
- In Burp Suite turn Intercept back to on.
Note
The firefox browser is being pointed to localhost as a proxy and therefore Burp may intercept the request.
- Submit another comment using something simple like “test” or “abc”.
- Burp should come back to the front, but if not switch to Burp to examine the request.
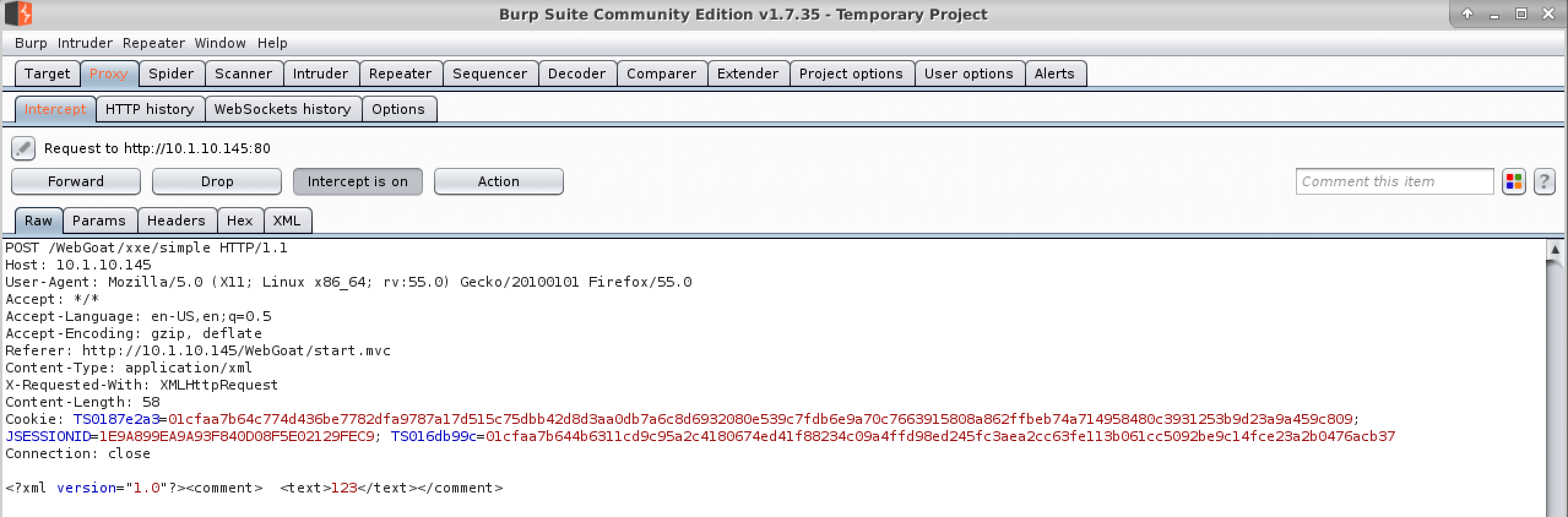
- Edit the request with the following XML.
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "file:///" >]>
<comment>
<text>abc&xxe;</text>
</comment>
There should be an XML document on your desktop named xxe which you may paste from to save time, but please read and understand the request.
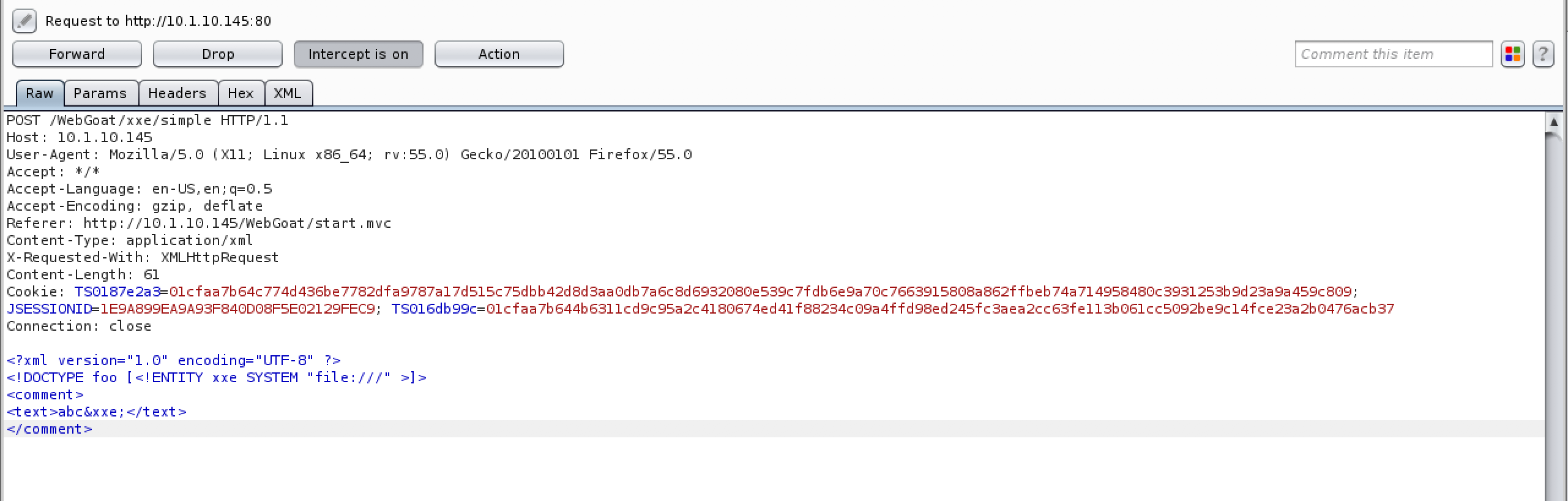
- Click Forward to pass the request on to the server and make sure you forward any remaining requests before turning intercept back off.
- What was the result?
Mitigate an XXE attack¶
- Login to the BIG-IP as before with admin/password.
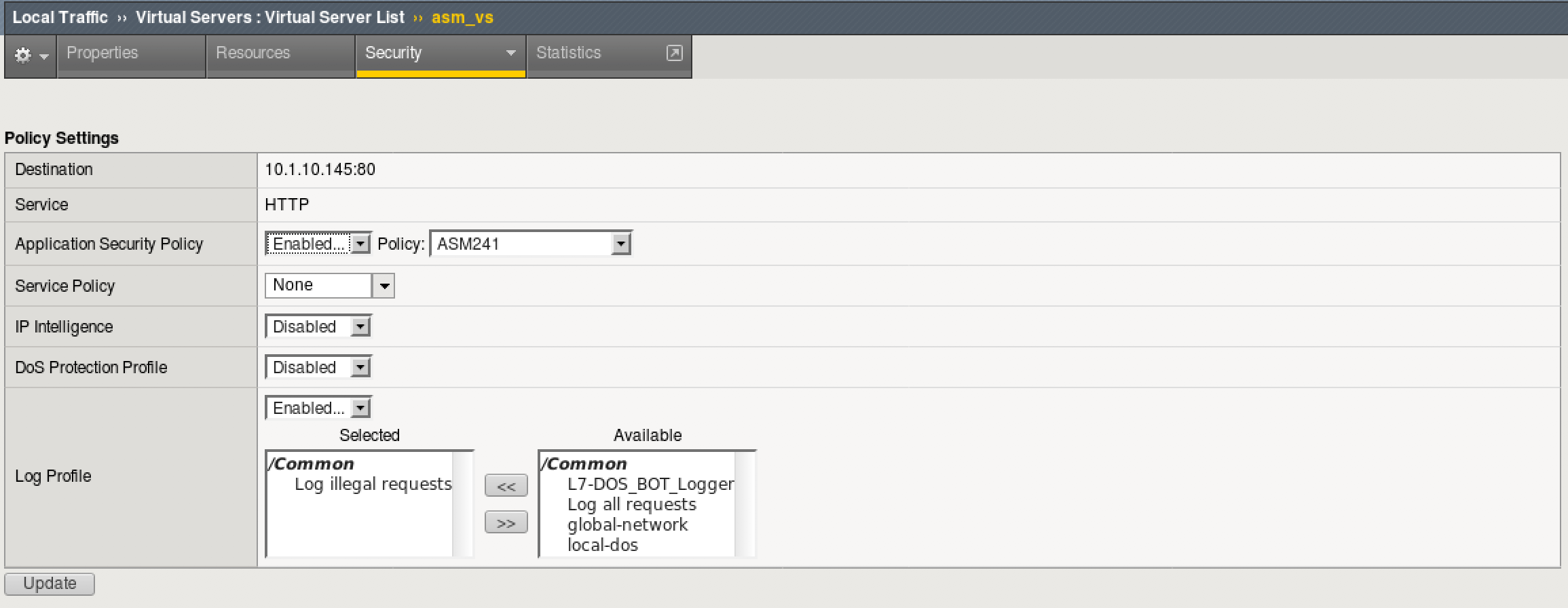
- Browse to Local Traffic > Virtual Servers > asm_vs and select “Policies” under the security tab.
- Make sure “ASM241” is selected as your Application Security Policy and that you have “Log Illegal Requests” as your Log Profile. Click “Update” if any changes are made.
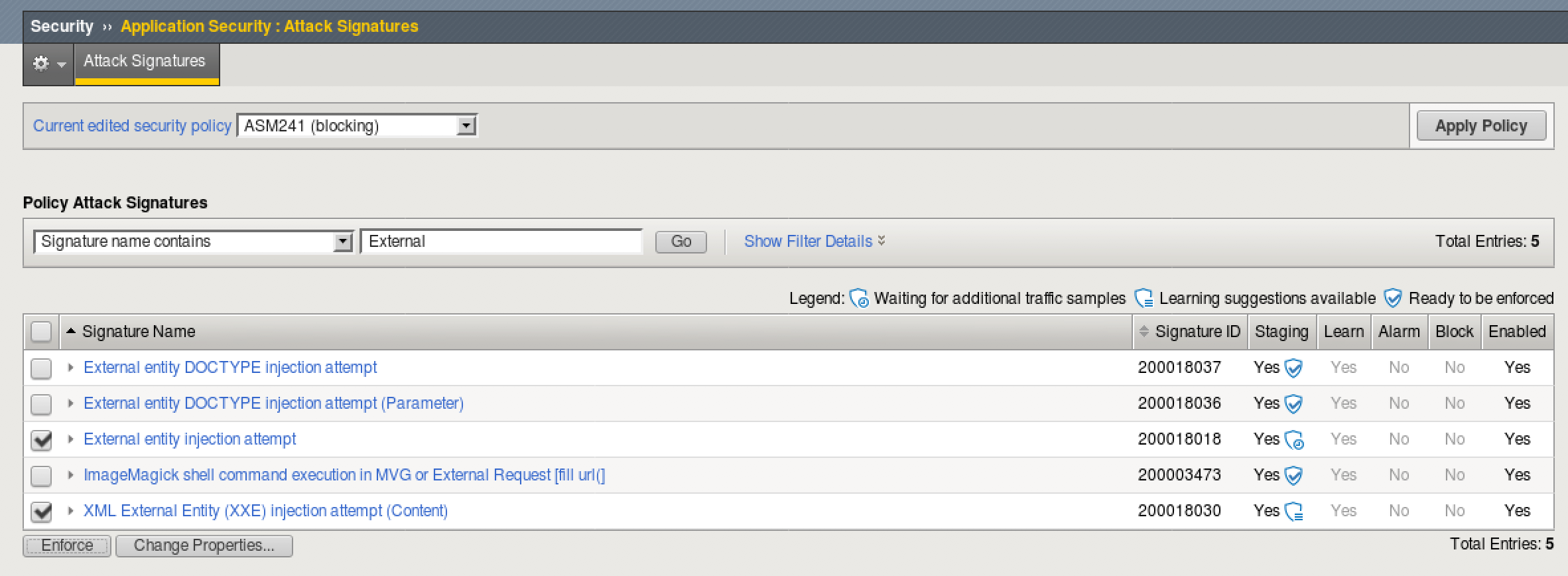
- Go to Security > Application Security > Attack Signatures and make sure your current edited policy is ASM241.
- Under Policy Attack Signatures, select “Signature name contains” and enter “External” before clicking Go.
- Select the following signatures and click enforce. Click “Apply Policy”.
- Using Burp suite and firefox, turn intercept back on we will run the same test, manipulating the request.
- Submit another comment that is different from the previous, something simple like “test1” or “abc1”.
- Burp should come back to the front, but if not switch to Burp to examine the request.
- Edit the request with the following XML.
<?xml version="1.0" encoding="UTF-8" ?>
<!DOCTYPE foo [<!ENTITY xxe SYSTEM "file:///" >]>
<comment>
<text>abc1&xxe;</text>
</comment>
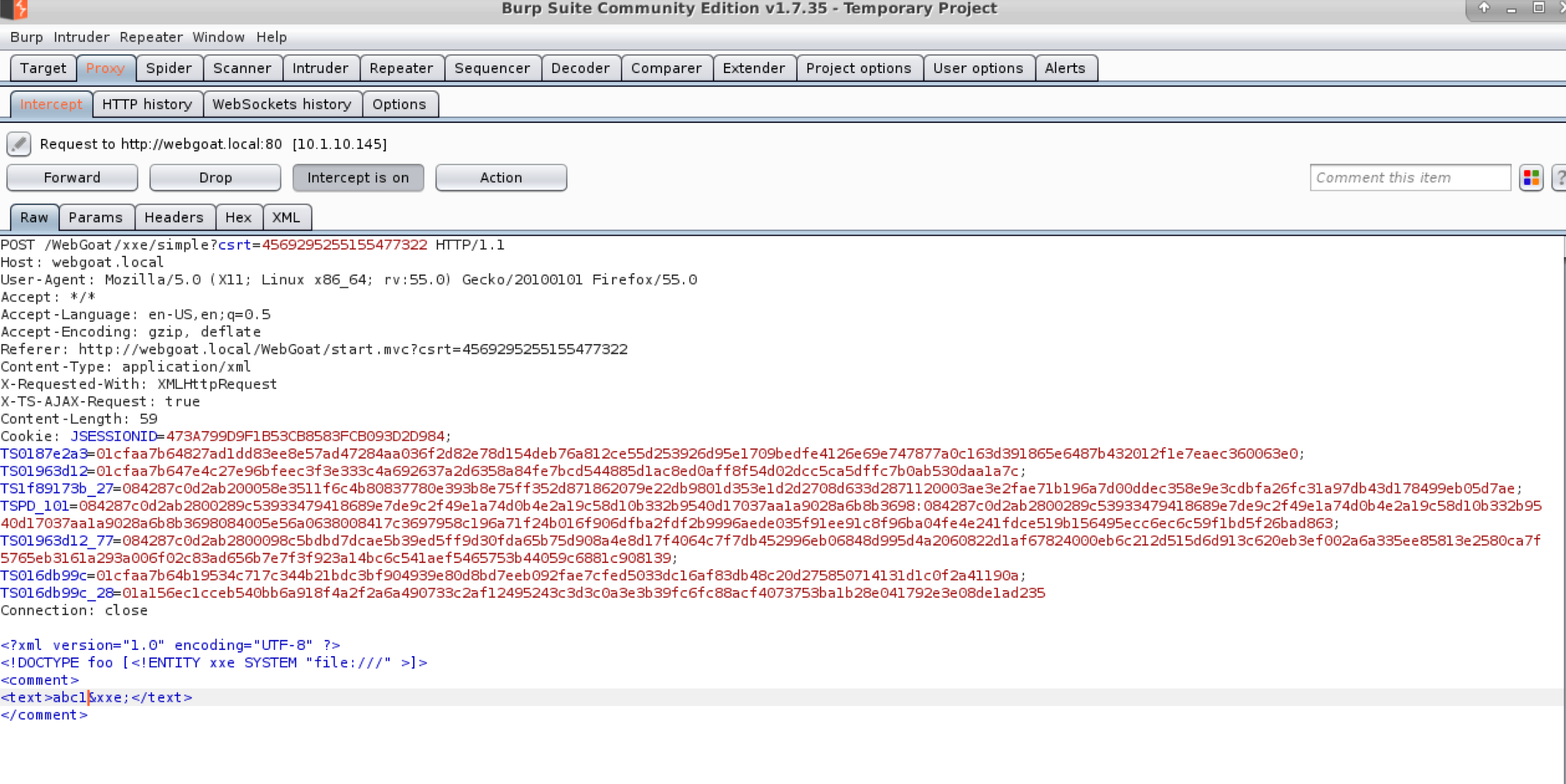
- Forward the request. What happens this time?
Check your logs¶
- On BIG-IP go to Security > Application Security > Event Logs > Application > Requests.
- You should see an entry that trigger the now enforced Attack Signatures.
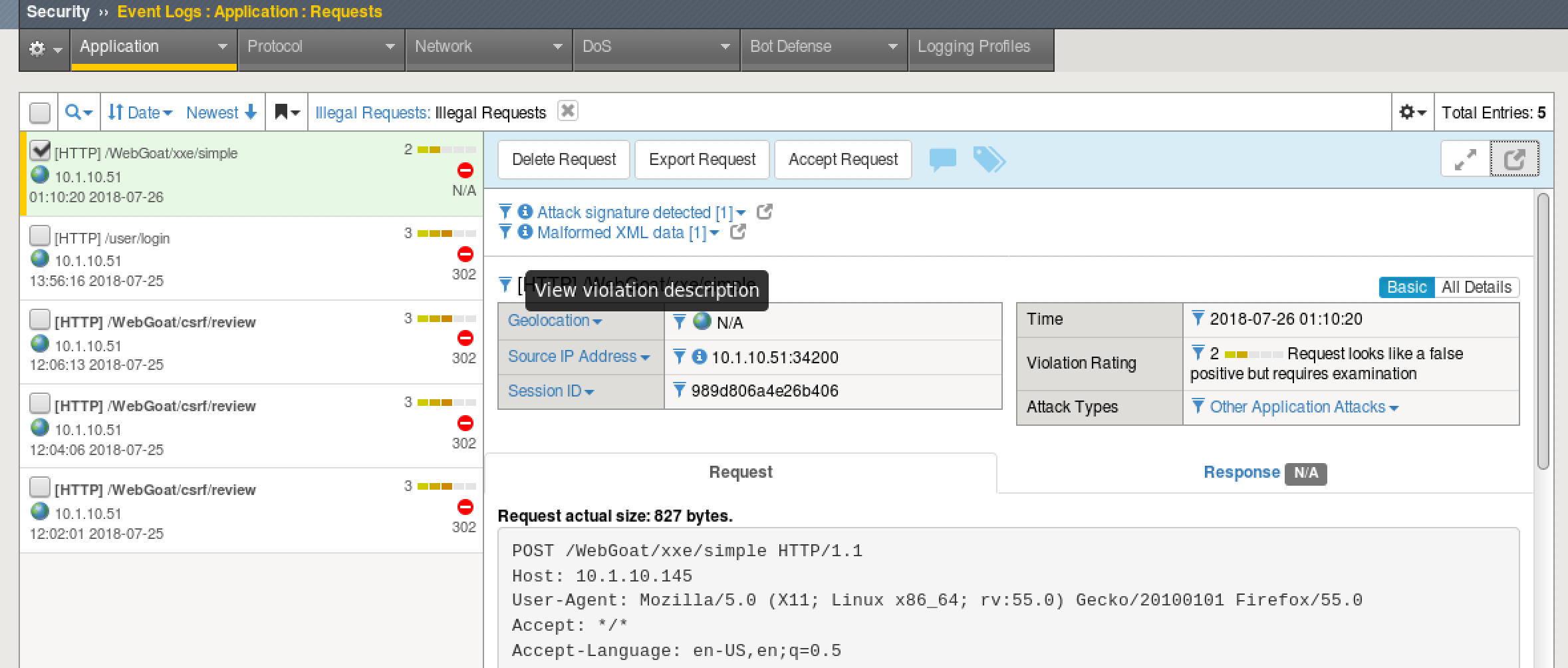
- What is another way that ASM could be used to mitigate XXE injection?
Hint: Take a look at the Application Security > Content Profiles > XML Profiles. The Default profile is applied to all http and https requests.
- Turn intercept back to off and close Burp Suite. Then return to your firefox settings and change the proxy settings back to “No Proxy”.