Lab 4: CSRF (Cross-Site Request Forgery)¶
This lab will simulate a Cross-Site Request Forgery against WebGoat Application. It is designed to show how ASM can mitigate similar real world vulnerabilities.
Connect to the Lab Environment¶
- From the jumphost, launch firefox, click the BIG-IP bookmark and login to TMUI. admin/password
- In separate tab connect to http://webgoat.local/WebGoat/login or click the bookmark and login as f5student/password
Test CSRF Behavior¶
In the WebGoat App, go to Request Forgeries, then click Cross-Site Request Forgeries
Click the tab/button for #4 and read through the lesson.
In this lesson you will use a common comment/review page for an online seller.
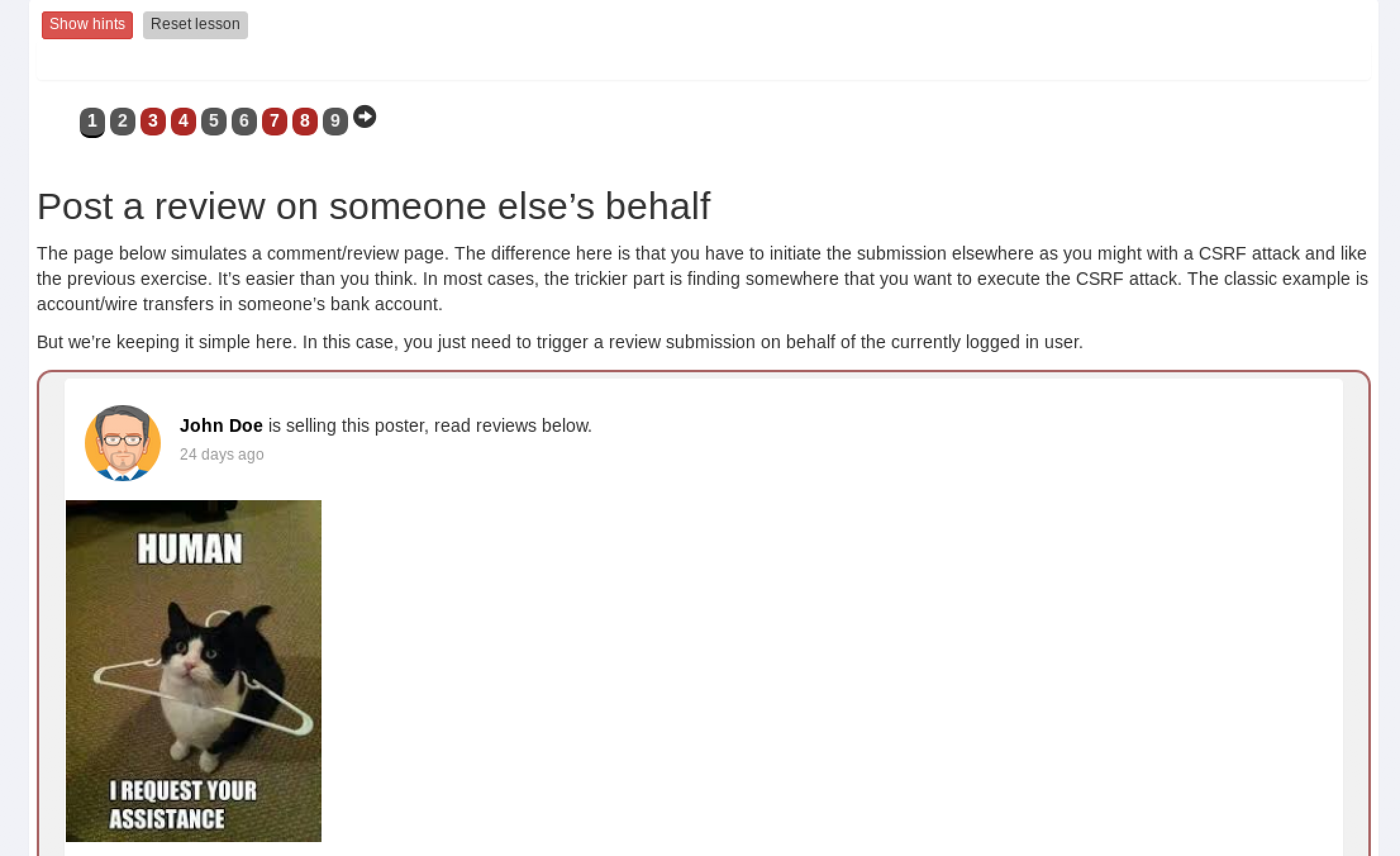
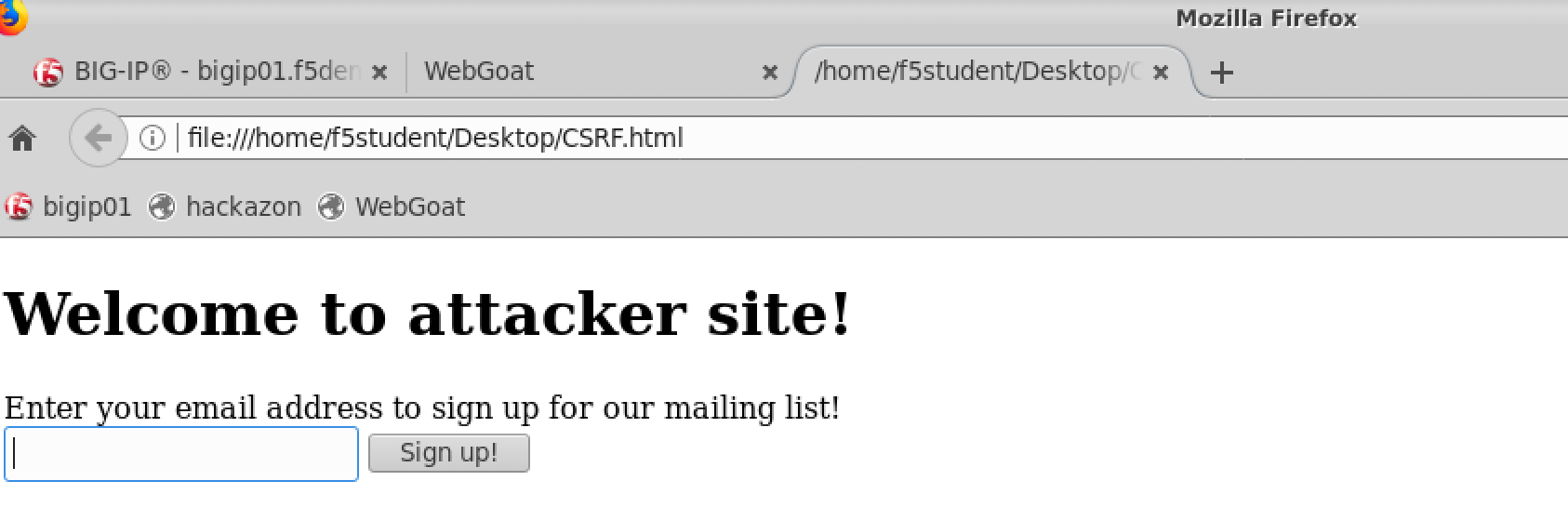
Minimize the browser and open the CSRF.html file on your desktop.
This is an example of a website asking you to register for a mailing list.
Type in “f5student@example.com” and click Sign Up. This should open a new tab, leave the tab open.
Note
This type of tab would not normally pop up upon a successfull CSRF attack and is purley here for illustration purposes
Click back on your webgoat browser tab. Then refresh (you ust refresh the page to view the changes) the reviews section. What do you notice?
The attacker site took advantage of the fact that you were already logged in to WebGoat Application and used your account to post a review.
Go back to the attacker site tab, right-click and select view source. Examine the code to see the hidden form fields that were used for the attack.
Mitigate the Attack¶
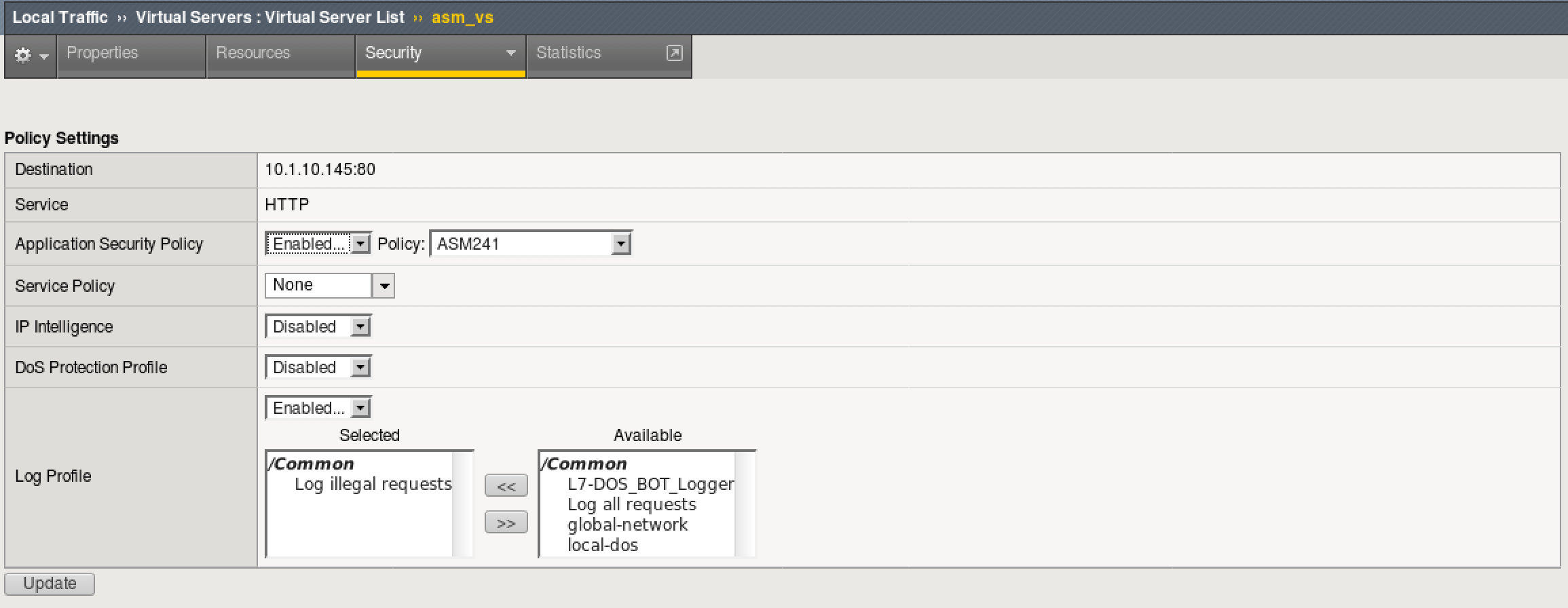
- Apply the ASM241 Security Policy to the asm_vs. On the BIG-IP TMUI, go to Local traffic > Virtual Servers > asm_vs
- Click the Security tab and make sure “Application Security Policy” is set to “asm241”.
- Make sure the logging Profile is set to “Log Illegal Requests”
- Click Update to apply the policy to asm_vs.
- Apply CSRF Protection to the ASM241 policy. Go to Security > Application Security > CSRF Protection, ensuring the “Currently edited security policy” is ASM241.
- Check enabled and in the New URL field type “/WebGoat/start.mvc*”
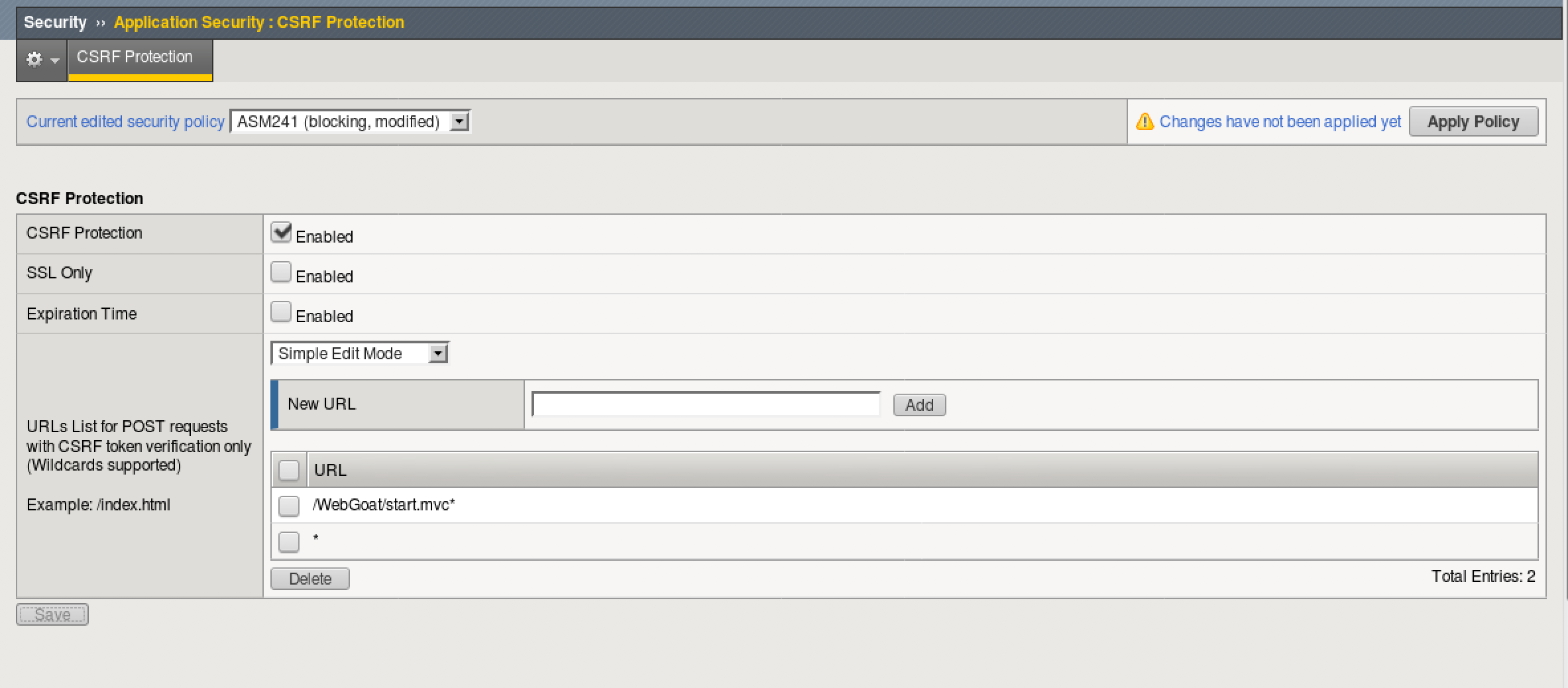
- Click Add and Save, then click Apply Policy in the top right and OK.
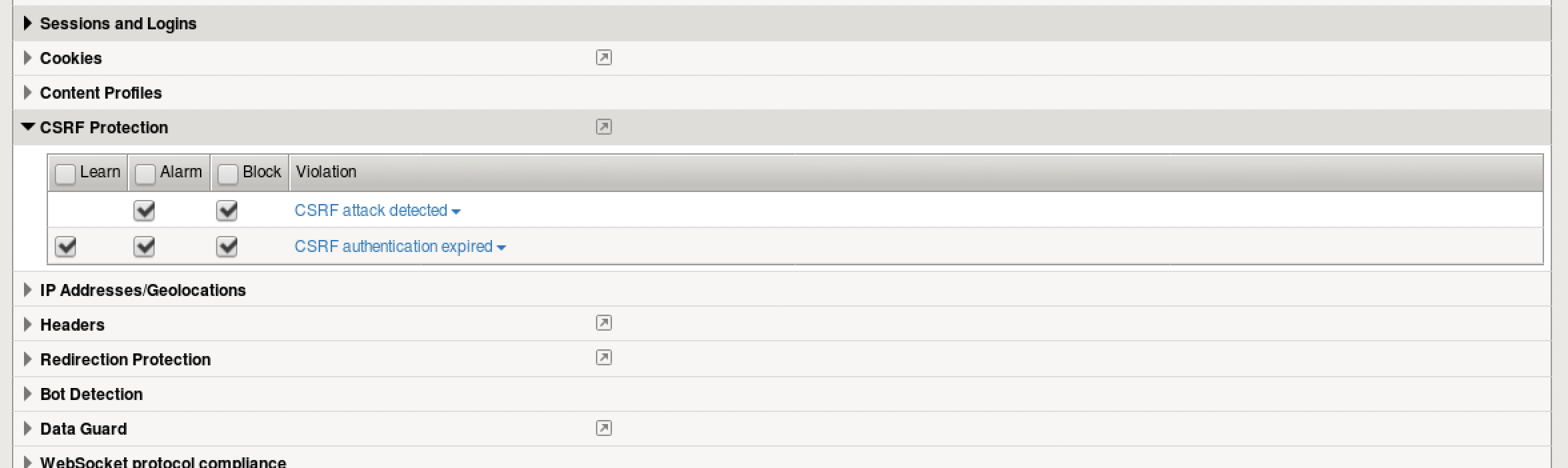
- Go to Security > Application Security > Policy Building > Learning and Blocking Settings and select “Advanced” in the drop-down on the right.
- Expand CSRF Protection and ensure all checkboxes are checked for “CSRF attack detected”.
Test the CSRF attack again¶
Browse to http://webgoat.local/WebGoat/login and login as “f5student”.
On the left menu click Request Forgeries, then click Cross-Site Request Forgeries.
Click the number “4” near the top of the page.
Open the “CSRF.html” file on your desktop again or click back on the “Attacker site” tab in your browser if it is still open.
Type anything into the text field and click the Sign Up! Button.
The request should be blocked by ASM
On the BIG-IP, go to Security, and click on Event Logs.
You should see the CSRF attempt blocked and logged