Exercise 4.0: HTTPS iApp with Policy¶
Overview¶
F5 offers a number of templated installations for various applications. For generic web based applications you can find the https iapp template. As an update to this template we have added security functions such as firewall and web application firewall policies that can be deployed with the application. In this lab we will focus on using the basic http iApp template. If you are interested in integrating similiar templates in to your automation and orchestration strategies please follow this training with the Application Services Lab located here:
http://clouddocs.f5.com/products/extensions/f5-appsvcs-extension/3/
Task 1 - Deploy iApp with Security¶
- Go to iApps > Application Services then click on Create
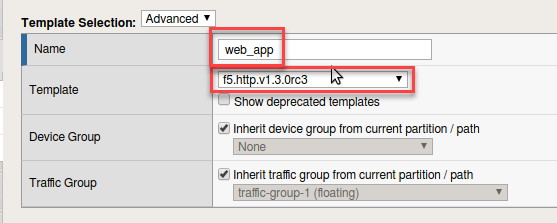
- Give the application a name
- In the drop down box for template choose f5.http.v1.3.Orc3 (also choose Advanced just above)
Note
This template has been imported for this lab. You will find this template at F5 Downloads. Follow this article on how to download: https://support.f5.com/csp/article/K98001873 The deployment guide can be found here: https://www.f5.com/pdf/deployment-guides/iapp-http-dg.pdf
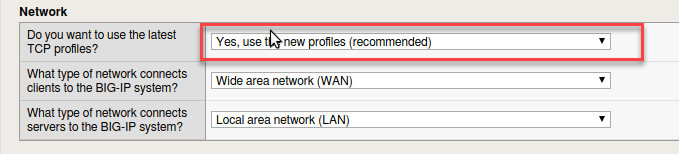
- New information appears below that will allow you to configure an application with web application security. In the network section answer Yes, use the new profiles.
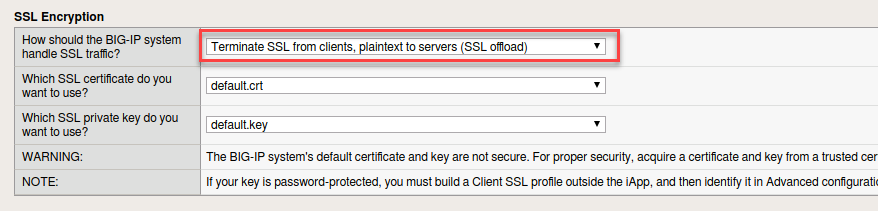
- In the SSL Encryption section select Terminate SSL from clients, plaintext to servers (SSL Offload)
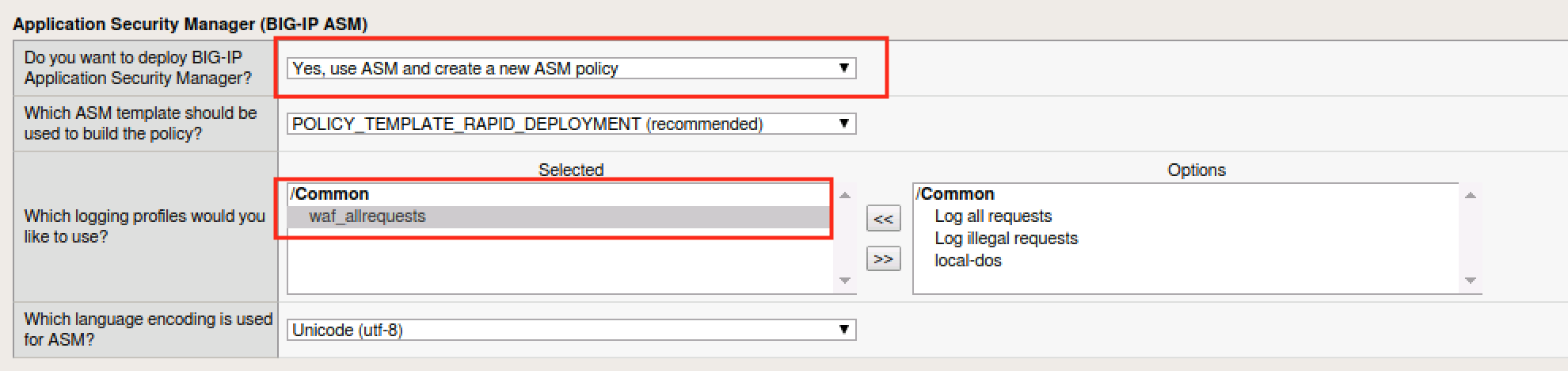
- In the Application Security Manager section select Yes, use ASM and create a new ASM policy. Also select the waf_allrequests logging profiles
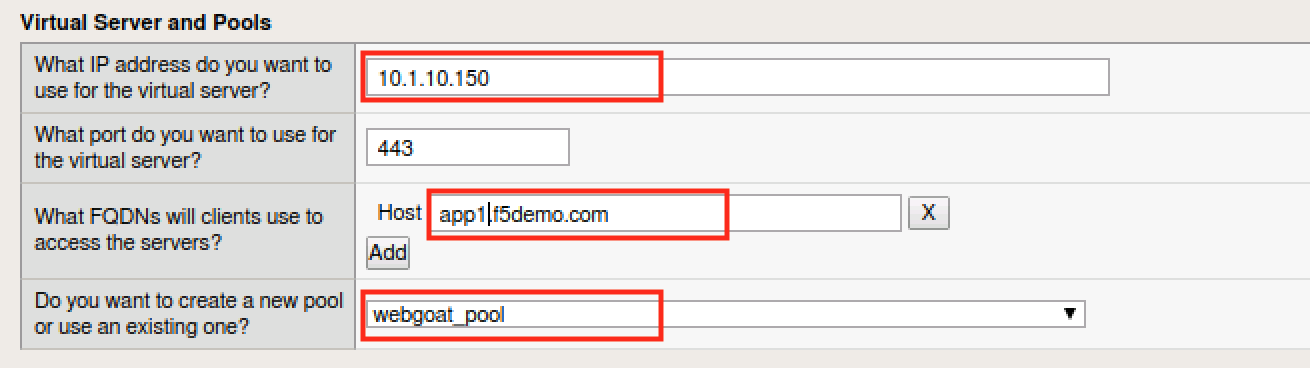
- In the Virtual Server and Pool section give the IP Address, an FQDN and select the webgoat_pool
- Click finished and have patience while the application objects are built
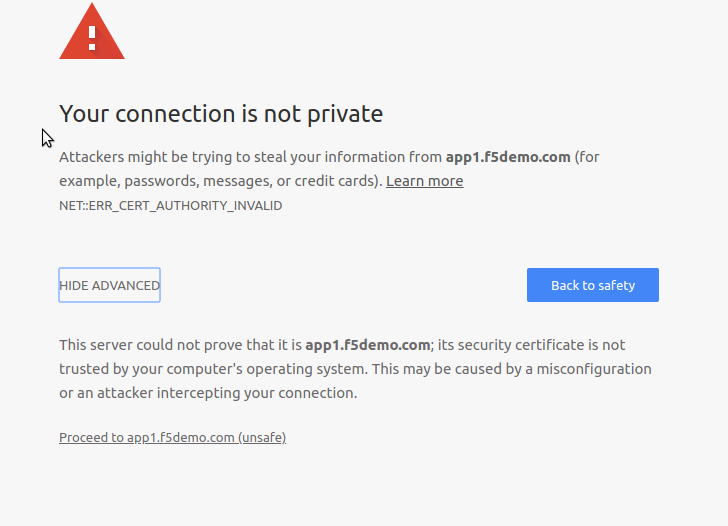
- Open a new icognito window in Chrome and click the app1 bookmark in the browser bar. When you get the SSL warning click Advanced and Proceed
- Login with f5student and f5DEMOs4u!
- You can try surfing around the application. Try an injection attack.
- Return to the BIG-IP. Go to Security > Application Security > Policy Building > Traffic Learning Select the new policy built by the iApp web_app_policy
Do you see learning suggestions? (Hint - there are none yet)
- Go to Security > Application Security > Policy Building > Learning and Blocking Settings
- Click the carrot by Attack Signatures then Change at the far right to add more signatures.
- Choose the High Accuracy Signature sets and SQL injection.
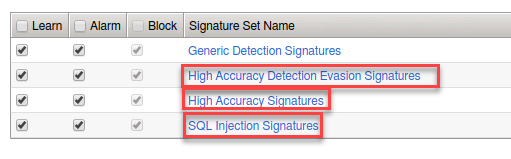
- Click Save and Apply Policy
Task 2 - Attack Application¶
- Within Chrome choose New Incognito window
- Click on the App1 bookmark to get to the WebGoat application
- At the username prompt try entering a sequel query for the username and the letter a for the password
or 1='1
Note
Did you see anything? Why do you think you were not blocked?
- Return to the BIG-IP Go to Security > Event Logs > Application > Requests and clear the illegal requests filter.
- You will find an level 3 alert there for the login page.
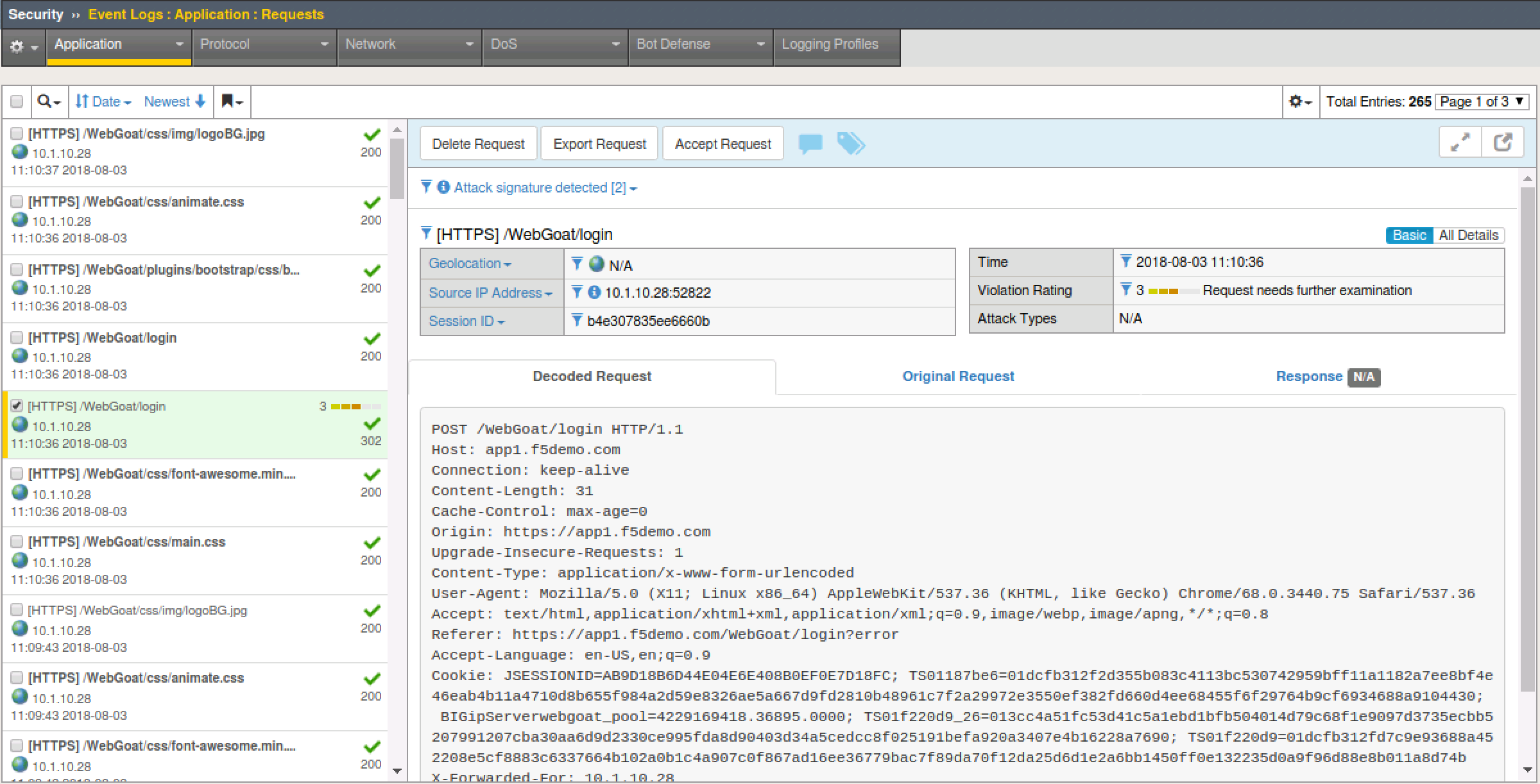
- Return to the WebGoat application and login with credentials f5student and f5DEMOs4u!
- From the left menu go to Injection Flaws –> SQL Injection and select exercise 7
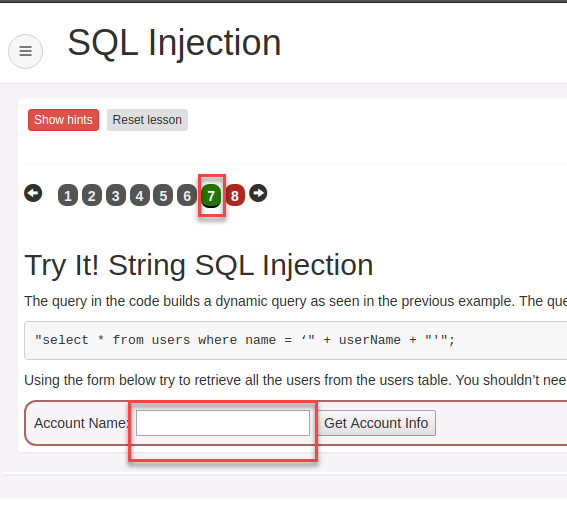
- In the account name field try an injection attack
%' or 1='1
Note
Were you blocked? Why or why not?
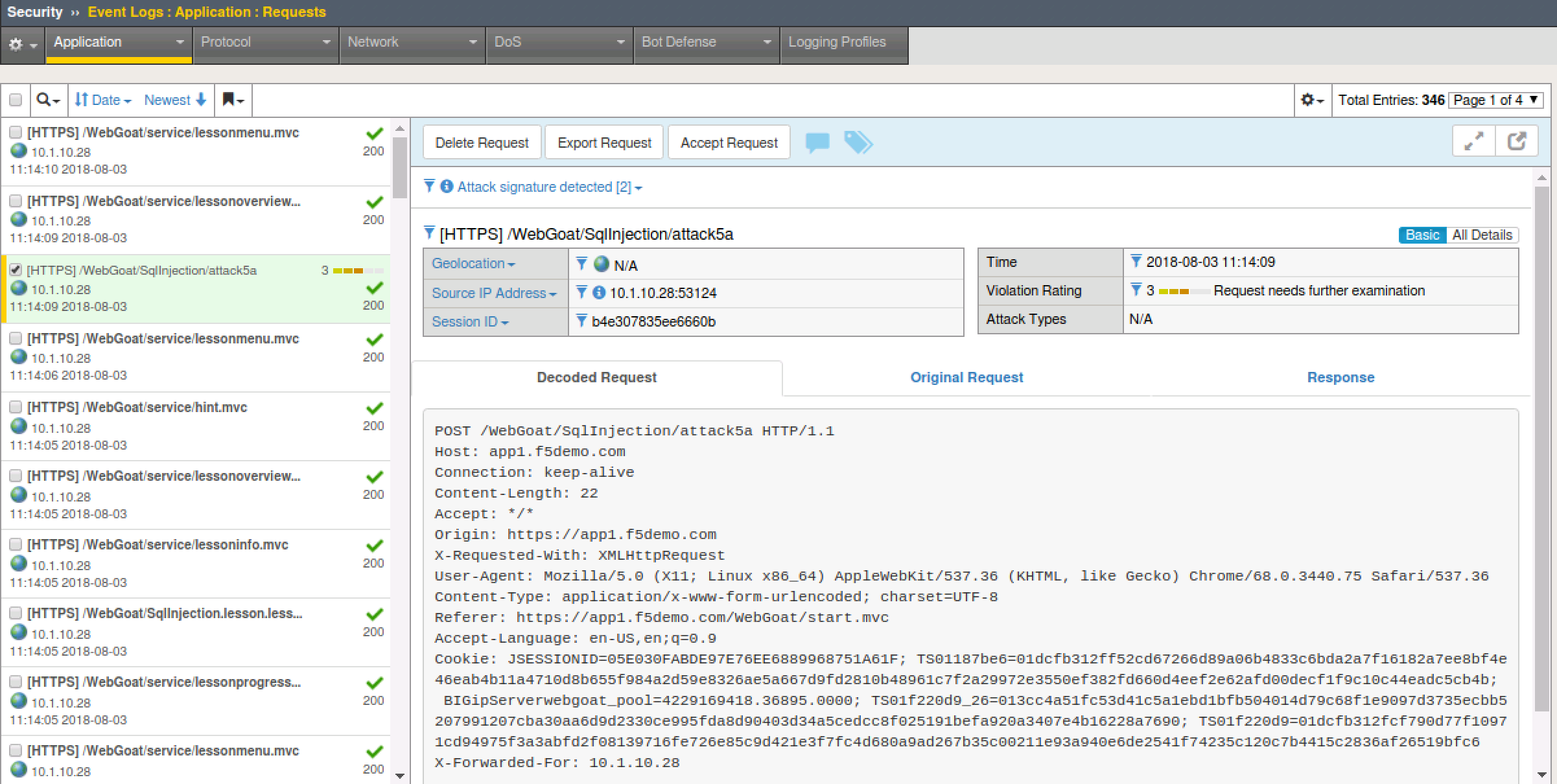
- Return to the BIG-IP Security > Event Logs > Application > Requests
- You will need to refresh. Locate the attacks. Is the policy in transparent or blocking? How can you change the policy to mitigate against this attack?